
Weekly Cyber News Roundup
September 25th to September 29th 2023
Content
01. News Bites
-
Critical libwebp Vulnerability under active exploitation with CVSS score increased to 10
-
Threat Actors claiming to have breached Sony. Sony launches investigation.
-
DarkBeam leaks billions of email and password combinations
-
New ZeroFont Phishing tricks outlook into showing fake AV-Scans
02. Conclusion
Critical libwebp Vulnerability under active exploitation with CVSS score increased to 10
Two weeks ago, Chrome along with other browsers were found to have a zero-day exploitation which was immediately patched. Tracked as CVE-2023-4863 at the time, had a High base score of 8.8 on the CVSS metric. As of the 26th September 2023, Google has assigned a new CVE, tracked as CVE-2023-5129 with a critical maximum severity score of 10. The problem has been linked in the Huffman coding algorithm which is used by libwebp for lossless compression.
With a specially crafted WebP lossless file, libwebp may write data out of bounds to the heap. The ReadHuffmanCodes() function allocates the HuffmanCode buffer with a size that comes from an array of precomputed sizes: kTableSize. The color_cache_bits value defines which size to use. The kTableSize array only takes into account sizes for 8-bit first-level table lookups but not second-level table lookups. libwebp allows codes that are up to 15-bit (MAX_ALLOWED_CODE_LENGTH). When BuildHuffmanTable() attempts to fill the second-level tables it may write data out-of-bounds. The OOB write to the undersized array happens in ReplicateValue.
The result of this new CVE has had major consequences for other developments using the libwebp open-source library. Making it official not a Browser vulnerability but an libwebp vulnerability. This vulnerability provides threat actors the capability to execute out-of-bounds memory writes, exploiting maliciously crafted HTML pages. Which can result in severe outcomes such as crashes to arbitrary code execution and unauthorized access to sensitive information.
This reclassification of CVE-2023-4863 to CVE-2023-5129 give the vulnerability a clearer description as to what the original underlying issue was, as this is a potential security risk for many applications that use libwebp, including all Web Browsers from Chrome to Safari, 1Password, Signal and the native Android Web browsers. As of the moment no patches have been made available.
Threat Actors claiming to have breached Sony. Sony launches investigation.
Sony have launched an investigation into the alleged breach of companies systems after ransomware group claimed to have exfiltrated data. The newly formed ransomware group or self-proclaimed “ransomware-as-a-service” group known as Ransomed.vc have claimed on both social media forums and dark web that they have “successfully compromised all of Sony systems”. Ransomed.vc also posted what kind of information they have stolen along a note stating “we wont ransom them! We will sell the data. Due to Sony not wanting to pay. DATA IS FOR SALE”.
Ransomed.vc has also posted proof of the exfiltration by including screenshots of internal log-in page, internal powerpoint presentation and a number of Java files, however the proof is seen as not convincing information that data has been exfiltrated. The group has also listed that if no purchases of the exfiltrated data, that they will post all of it on 28th September 2023. As of writing this article no data has been leaked.
However, posted on the 26th September on BreachForums by MajorNelson was a small free sample of a 3.14GB data that is claimed to belong to Sony. With contents listed as “a lot of credentials for internal systems” and other folders relating to internal information. However, investigations have not yet shown definitive answers.
Prior to this claimed breach, the last major incident that Sony encountered was in 2014 by North Korean threat actors on Sony Pictures to stop the release of the film, The Interview.
DarkBeam leaks billions of email and password combinations
DarkBeam is a digital risk platform, which captures and stores credentials from other data leaks and stored them in an Elasticsearch database. On September 18th 2023, this database was shown to be exposed to the internet with no credentials required to access. The database was reported to contain over 3.8 billion records containing username and password credential combinations in plain text format.
While some of these records were available in disparate locations on the clear and dark web, the DarkBeam data set has been aggregated into a single repository of credentials, which would make it trivial for threat actors to acquire and abuse. This is similar in nature to the “RockYou21” password list, which was compiled from other data leak sources and released intentionally.
This is especially worrying given that the purpose of DarkBeam is to indeed protect organisations from the effects of credential leaks and highlights the often-overlooked aspect of operational security within cyber security companies. Security professionals are often granted unfettered access to highly sensitive information as part of their role, and it’s ultimately important that they maintain control over this data at all times.
If you believe you or your organisation has been affected by a data leak, online leak checking tools can be used to verify individual accounts by supplying the e-mail address of the account. For more in-depth protection for organisations, consider a dedicated risk protection service, such as Integrity360’s Digital Risk Protection Service (DRPS).
New ZeroFont Phishing tricks outlook into showing fake AV-Scans
Cyber criminals are becoming increasingly creative when it comes to social engineering. In this new technique, they’ve started taking advance of zero point fonts to add custom anti-virus scanning messages to emails so that they show up in the email preview, but not the email body. For example in the below screenshot, you can see the grey message that the email has been “Scanned by Microsoft Defender and deemed safe.”, but this is actually just part of the body of the email. Microsoft Outlook automatically takes the first line of the email and shows it in the preview box below the Sender and Subject.

This is what the actual email looks like. As you can see the text above does not “exist” in the body.
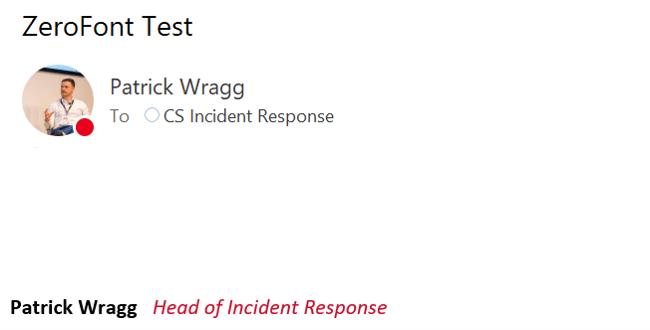
The purpose behind this new technique is to inject a sense of ease into the target and make them think the email and/or attachment is safe as it’s been “scanned by anti-virus”.
If you are worried about any of the threats outlined in this bulletin or need help in determining what steps you should take to protect yourself from the most material threats facing your organisation, please contact your account manager, or alternatively Get in touch to find out how you can protect your organisation.
Disclaimer
The Threat Intel Roundup was prepared by Integrity360 summarising threat news as we observe it, current at the date of publishing. It should not be considered to be legal, consulting or any other professional advice. Any recommendations should be considered in the context of your own organisation. Integrity360 does not take any political stance in the information that we share. Moreover, the opinions expressed may not necessarily be the views of Integrity360.
Need advice?
If you are worried about any of the threats outlined in this roundup or need help in determining what steps you should take to protect yourself from the most material threats facing your organisation, please contact your account manager or fill in the form for a complimentary no-commitment consultation.
More detailed threat intelligence news?
If you’d like more detailed threat intelligence news, Integrity360 offers this as part of our security monitoring managed services.
We also offer a tailored threat intelligence monitoring service for your organisation that actively monitors for threat actors and campaigns of direct relevance to your organisation, brand damage, copycat & spoofed domains, credential leakage and dark web monitoring.

Cyber Security Conference
STOCKHOLM | 17 October 2023
Integrity360's flagship conference Security First comes to Stockholm in 2023!
Join leading cybersecurity experts from across the community as we explore the latest threats and industry trends, and learn practical strategies to safeguard your organisation.


